Keeping us safe from cyber threats
As our lives become ever more reliant on digital technology it can feel just a matter of time before we fall victim to cyber crime. Researchers at Bath are taking on this menace.
“We’re caught in a cycle of patching and mitigating the vulnerabilities of our current computer systems to cyber security threats."
"Re-imagining hardware design, with new in-built security, opens the possibility of a secure and trusted digital future.
“Our research is about understanding people’s attitudes to cyber security and using that knowledge to drive a wider appreciation of why security matters. To make it easier to get on board with.
"Without sign up, society and business cannot benefit from technological advances coming our way.”

Redesigning digital security from the bottom up
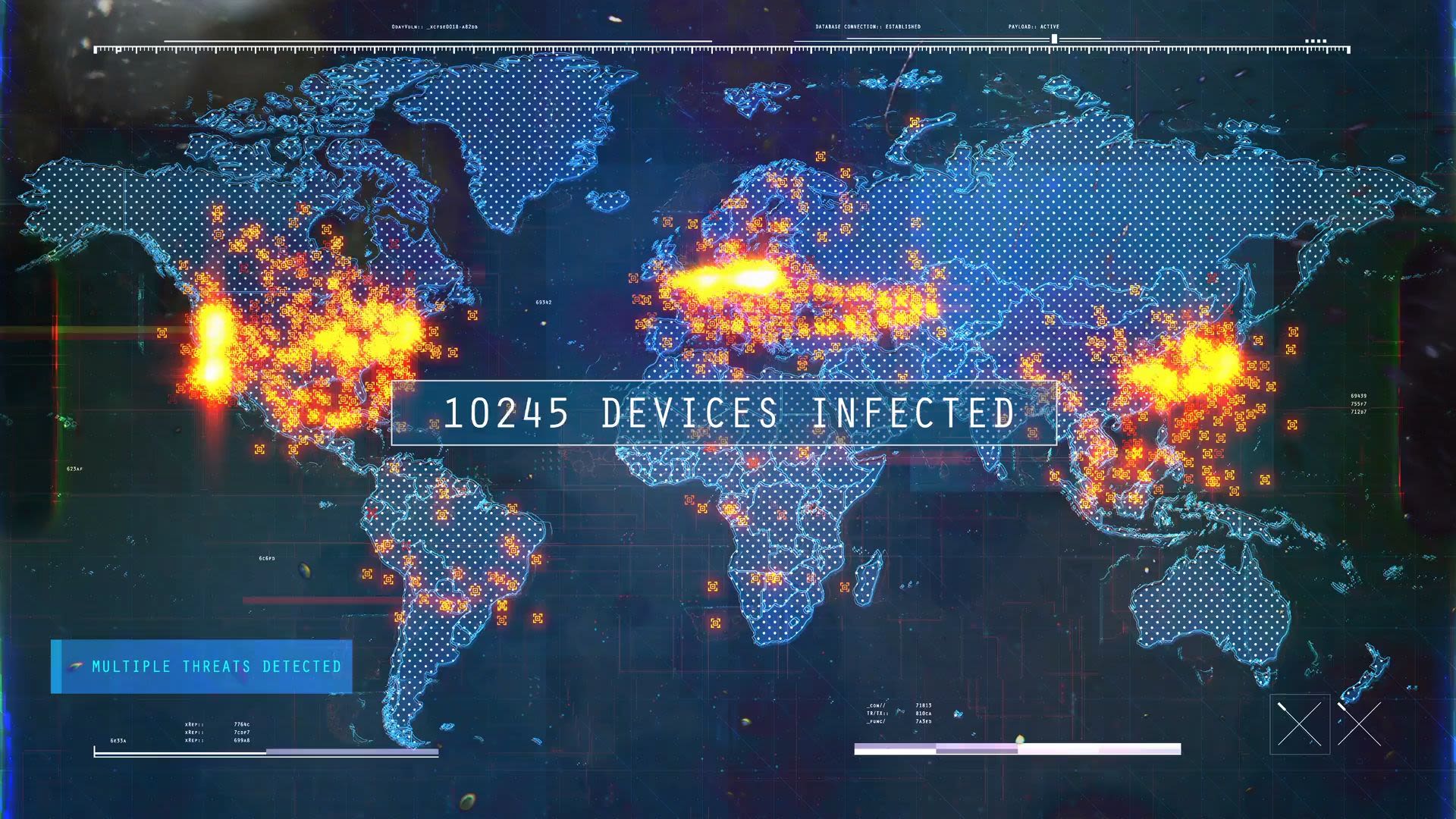
Businesses, organisations, critical national infrastructure and individuals are all in the line of fire from increasingly complex, sophisticated and severe cyber threats.
From data breaches to ransomware demands for money; state actors, criminal groups and activists are masterminding a tidal wave of cyber attacks, inflicting billions of pounds worth of damage on the UK economy.
Across the world, the threat pervades health care systems, food and energy supply chains, education, financial companies and markets: all of life is at risk from cyber threats designed for disruption and devastation.
More than 75% of UK businesses were affected by ransomware in 2021
The average cost of recovery was $1.85 million in 2021

When today’s cyber criminals target our digital systems, they’re exploiting vulnerabilities in our computer systems that trace back to the designs of the first microprocessors from the 1970s.
Developed well before the sophisticated cyber security threats we now face, the weakness of this hardware to modern cyber attack is an ever present challenge that organisations, big and small, as well as individuals, must grapple with to keep data and systems safe.
According to the Government's National Cyber Strategy 2022, 70% of current cyber security vulnerabilities exploit hardware flaws.
Yet security typically isn’t something that organisations prioritise. That is, until something goes wrong. For businesses, that ‘something’ can be catastrophic.
Eye-watering costs, combined with reputational damage and organisational upheaval. Fallout for clients and customers, financial loss, PR crises, as well as simply being unable to function. Factor in competitors jockeying to capitalise on another’s misfortune and security breaches can be devastating.
Researchers at Bath's School of Management are trying to change the focus on cyber security. They are part of a £190million project which is taking digital security back to the drawing board: to design a safer, more resilient future. The Digital Security by Design (DSbD) programme is developing a new, secure hardware and software ecosystem that incorporates digital security from the outset.
“It’s a revolutionary approach to cyber security that is successfully engaging hardware and software developers to work in tandem to transform the sector and offer a safer, trusted, resilient future for digital technology.”
Bringing together government, industry and academia, the project is stepping away from the cycle of cyber attack and software patch to build-in modern digital security to hardware and software design from the ground up.
Newly designed microprocessors, already in development by technology partner Arm, will implement an approach developed at the University of Cambridge.
It will provide protection from commonly exploited vulnerabilities by better managing the allocation of memory and data access at the hardware layer of the computer system.

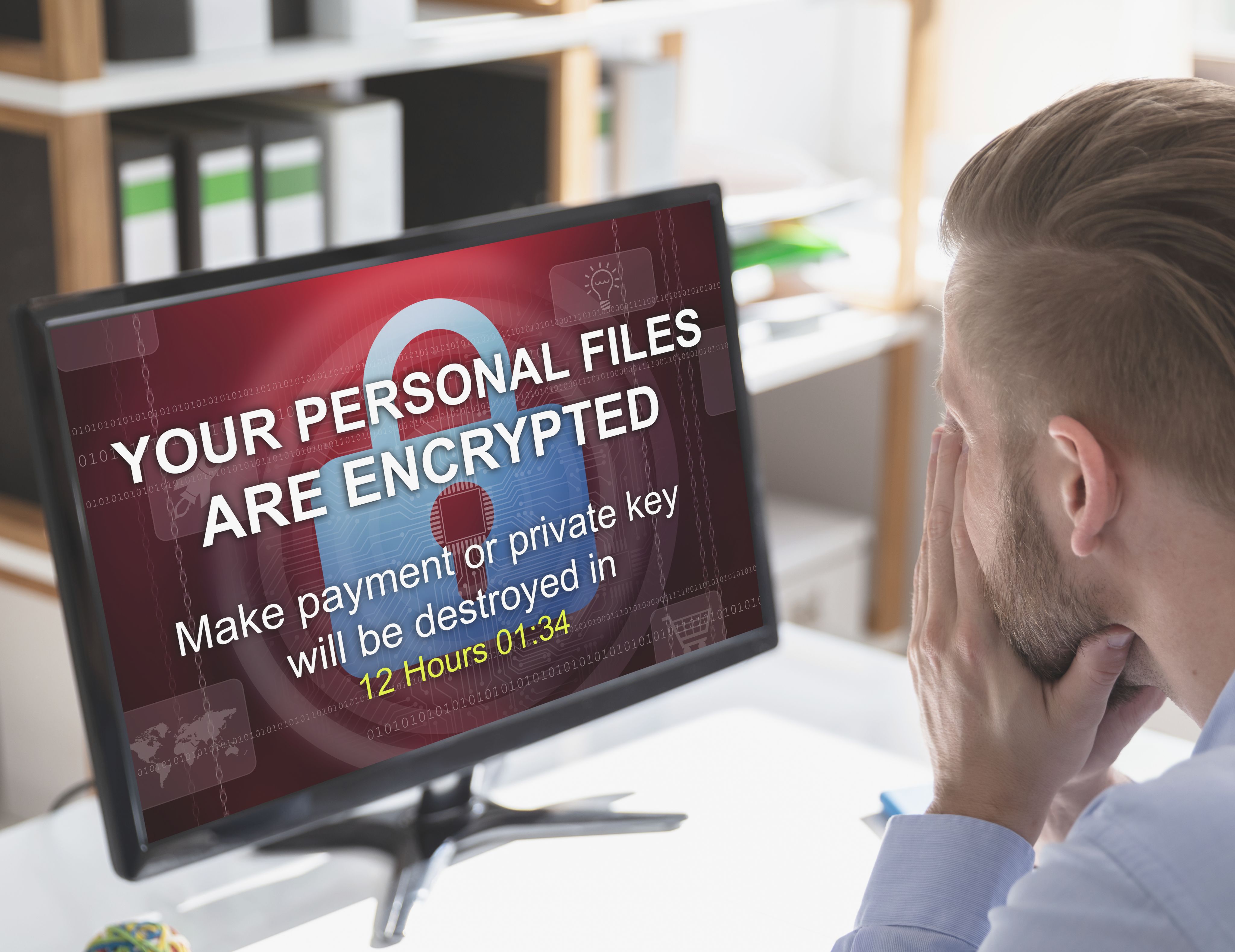
Under attack

The number of ransomware attacks reported to the Information Commissioner’s Office increased 100% from 326 in 2020 to 654 in 2021, according to a report by international law firm RCP.
Hackers encrypt vital data and demand a ransom in order to get the information decrypted.
Industry sectors most frequently impacted by attacks in 2021 included: finance, insurance and credit; and education and childcare.
Negotiating with cyber criminals is strongly discouraged by governments and industry but 82% of British firms who have been victims of ransomware attacks have paid the hackers to try and get data back.
Only half regained access to data and systems after the first payment.
In 2017 the Wannacry ransomware attack targeted computers worldwide, encrypting data and demanding ransom payments in Bitcoin cryptocurrency. The attack affected a third of NHS trusts and cancelled approximately 7,000 appointments.
Scottish multinational engineering company Weir Group was hit by ransomware in September 2021, forcing it to shut down its IT systems, enterprise resource planning operations, and engineering applications. It cost £5million in direct losses and the Group predicted indirect losses costing ten times as much.
In October 2020 Hackney Council suffered a ransomware attack which caused many months of disruption and cost millions of pounds to rectify. The council was locked out of important data and many services were disrupted, including council tax and benefit payments.
A ransomware attack against the Irish Health Service Executive in May 2021 disrupted Irish healthcare IT networks and hospitals for over 10 days, with consequences for patients and families. Stolen patient data was published online.
Phishing attacks remain the key route for hackers to access networks. They lure employees to click on a link in an email containing malware - malicious software designed to corrupt, steal and cause havoc.
Foiling phishing attacks
Exploiting a sense of urgency and invoking authority are some of the hallmarks of phishing attacks – pressuring individuals to respond to fraudulent emails requesting personal or confidential information, for malicious use.
This insight into what makes people susceptible to phishing and targeted ‘spear’ phishing emails was gathered by Professor Joinson and his team, leading directly to improvements in national cyber security.
The research supported the development and implementation of the UK government’s Don’t take the bait awareness campaign and National Cyber Security Guidance called Phishing Attacks: Defending Your Organisation published in 2018.
It was taken up by key national security bodies including the Centre for the Protection of National Infrastructure and the National Cyber Security Centre, changing organisational practice on phishing training at organisations including the Bank of England, BAE, Airbus, HMRC and the Home Office.
The research:
- What (if any) behaviour change techniques do government-led cybersecurity awareness campaigns use? Read
- Developing a measure of information seeking about phishing Read
- Exploring susceptibility to phishing in the workplace Read
- Press accept to update now: Individual differences in susceptibility to malevolent interruptions Read

More than a tech problem
Computer platforms that are more secure will benefit all industries operating in the digital world, from financial services and manufacturing; to transport, healthcare and education. But will technology companies and ultimately businesses and consumers want to adopt the DSbD future?
Cyber security research at Bath is engaging social scientists and management researchers in new ways. Professor Adam Joinson is Director of the DSbD Discribe Hub+ at Bath. The research programme is applying social science and economics expertise to influence hardware design and, for the first time, helping to shape the digital spaces that people use for work and commercial activities, as well as living their day-to-day life and socialising with friends and family.
“We’re creating a better collective understanding of the future context for the next generation in digital security technology. One that will inspire successful development of digital systems and wide scale adoption,” he says.
“Funded by ESRC, Discribe is bringing together a community of technologists, regulators, business and end users, along with social scientists and arts and humanities academics from four leading UK universities – Bath, Bristol, Cardiff and Royal Holloway. It’s drawing on diverse thinking with the end goal of creating digital technology of the future that people can trust.”
The prototype DSbD Morello board, developed by Arm, is anticipated to be several years away from use in everyday devices, phones or laptops. Without an existing product to study, Discribe is drawing on arts and humanities researchers and professionals to look to the future and envisage the required protection and decisions that businesses will make.
Breaking barriers to a more secure future
“The success of the DSbD initiative will partly be determined by the speed and breadth of adoption by businesses. Understanding what’s on offer, incentives to get on board with it, and the costs of adopting new secure architectures are key,” says Prof Joinson
While the wider DSbD programme is developing the hardware, the focus at Bath is on how to ensure the new technology is adopted. What makes businesses and organisations adopt new security practices?
It leads to an age-old question that Prof Joinson’s collaborator Dr Joanna Syrda is exploring: like insurance, how do you value the absence of something? How do you generate interest and uptake in something that ultimately prevents and protects against a threat occurring?

“How do we convince consumers and companies that they’ve benefited from cyber security investment when there’s ‘nothing’ to show for it?” asks Dr Syrda, business economist at Bath’s School of Management, and research lead.
“Valuing the absence of a cyber security breach for your own organisation is already a problem, but when you add in how to rate the absence of security impacts for other people along the chain, it’s an extra layer of complexity.
“Positive or negative cyber security behaviour by businesses can have implications on others, which businesses don’t pay for. We’ve seen this at play through the huge rise of supply chain attacks, where companies that haven’t taken sufficient security measures can impose terrible consequences for their clients, or other supply chain links.”
Dr Syrda is applying economic thinking to cyber security, to develop and test new models that integrate economic modelling and human decision-making. Her goal is to model optimal levels of investment in cyber security for businesses. To understand how far we are from that sweet spot and to identify drivers and barriers to investment.
“We want to account for not only the private cost and benefit but the societal impact – what makes sense for a particular company and also for everybody else. So that we start to see cyber security as a social responsibility or public good, just as we would investing in clean air.”
An important part of the model will be understanding barriers to investment and also enablers, whether that’s taxes, subsidies, regulation or developing new social norms that support the idea of cyber security as a public good.
Game on
Investment in one area of the business inevitably involves a trade-off for another. That decision will be played out in a startup cyber security board game that researchers at Bath are devising.
Inspired by Decisions & Disruptions, a tabletop/ role-playing game about security in industrial control systems created by researchers at the University of Bristol, the team will develop the business game to explore the balance between cyber security and business investments, and how this dynamic changes with increasing business scale.
“We’re developing game scenarios in which players will be invited to imagine themselves as the CEOs of a smart healthcare startup. The game will be set up as a decision-making exercise where various investment choices will lead to different outcomes in terms of both cyber security and business growth,” explains Kseniya Stsiampkouskaya, research associate working on the project.
“For a growing company there are questions about how they balance investing in their business, establishing their product and expanding market share, with spending on security.
“Not investing in security might not have an immediate impact, but over time we may well build up a ‘security debt’ that actually ends up being repaid through increased vulnerability in some form or other.
“To understand this phenomenon better and identify optimal investment solutions, we’re planning to study startup decision-making by observing how players make their business and cyber security choices in the game and how they react to the consequences of those choices.”
For Discribe, the win will be understanding in more detail how business decisions can be influenced. Perhaps through regulation, through policy changes, new procurement practices or changing social norms.
Changing minds
Discribe is at the beginning of its cyber security ambitions but is already making an impact on the way the DSbD programme thinks about cyber security, an influence which is seen in the government’s National Cyber Strategy 2022,” says Prof Joinson.
“We’re seeing a new appreciation of the pressures on organisation in terms of the balance between making something perfectly secure versus getting the job done.
“Security doesn't necessarily sell that well, unless you're Volvo. It's rare to see security and safety as a core thing. We certainly don’t often think about the processors in our laptops or other devices, but lots of attacks are against hardware now.
“We can patch software, we can update it, we can keep an eye on it. You can't do that for computer hardware, and this is why it's so important, but also why it's actually quite difficult to explain and communicate.”
Discribe has identified communication as a major challenge, and shares programme partner Microsoft’s view that cyber security goes beyond being an engineering challenge, to a communication one around getting people to value security and adopt new technology. Discribe hopes to encourage that shift in thinking.
For many employees, cyber security is not a priority. Privately, it’s more likely to be viewed as something that stops them achieving their goals. Frustrated by the policies and procedures that security protocols impose, large numbers of people choose to ignore security updates.


Art against cyber crime
Researchers are using art to tell their story. They worked with artist Chris Day to illustrate their message of a new approach to cyber security.

“The beauty of DSbD is that we can tackle so many of the vulnerabilities that we’re currently living with. There'll still be a role for us as humans to be aware, but it will reduce,” says Prof Joinson.
Putting these words into pictures has helped to engage new audiences and networks.

For Prof Joinson, there’s a simple analogy. “When you're driving, you shouldn't have to think every moment ‘are my brakes working’ or ‘will my lights come on’? You trust the machine, and so long as you maintain it and do the usual occasional checks you can just concentrate on driving.”
He argues that people shouldn’t have to spend their working day scanning the horizon for threats. Instead, the technology should allow them to focus on getting the job done so long as it’s properly maintained and updated. Yes, there will always be vulnerabilities, but there should be a level of trust that takes away the fear and the burden of responsibility from the user.
While Prof Joinson and his team have already played their part in equipping individuals to be alert to cyber security attacks, his focus now is on handing some of the responsibility for security back to the engineers.
“We can no longer keep pushing the message of caution and eternal vigilance – ‘don’t click on this’, ‘don’t open that’. We have to be able to do our jobs. It's much better if we can be resilient and accept that sometimes something will happen, but know the systems are in place to mean that the situation is not irretrievable and any damage will be contained.
“In prehistoric times, if we spent 100% of our time worried about sabre-toothed tigers, we would starve, while those who ignored the risk would be eaten. We've evolved to balance being cautious and aware of potential threats with being able to take advantage of opportunities and get on with things. That's what we have to do when it comes to cyber security.”
Researchers at Bath are helping to create a new cyber security balance – combining awareness with trust and confidence. So that businesses can get on with their business - share data and information securely and focus on what matters to them.
And similarly, individuals can take advantage of all the possibilities of modern digital technology without the terror of falling prey to a cyber security attack.
“Monitoring, surveillance, control: none of these approaches work,” concludes Prof Joinson. “Trust matters and ultimately it is informed by vulnerability.
"Our role as researchers in the cyber security sphere is to give people confidence in a trusted digital future.”


Research papers
What (if any) behaviour change techniques do government-led cybersecurity awareness campaigns use? Van Steen, T.,Norris, E.,Atha, K.&Joinson, A.,2020,In:Journal of Cybersecurity.6,1, tyaa019
Developing a measure of information seeking about phishing Williams, E. J.&Joinson, A. N.,2020,In:Journal of Cybersecurity.6,1,16 p., tyaa001
“It wouldn't happen to me”: Privacy concerns and perspectives following the Cambridge Analytica scandal Hinds, J.,Williams, E. J.&Joinson, A. N.,30 Nov 2020,In:International Journal of Human-Computer Studies.143, 102498.
An Exploratory Study into the Negotiation of Cyber-Security within the Family Home Muir, K.&Joinson, A.,12 Mar 2020,In:Frontiers in Psychology: Human-Media Interaction.11, 424.
What is 'Cyber Security'?: Differential Language of CyberSecurity Across the Lifespan Jones, S.,Collins, E.,Levordashka, A.,Muir, K.&Joinson, A.,2 May 2019,CHI EA 2019 - Extended Abstracts of the 2019 CHI Conference on Human Factors in Computing Systems.Association for Computing Machinery,Vol. 2019-May.6 p.3312786
Exploring Susceptibility to Phishing in the Workplace Williams, E. J.,Hinds, J.&Joinson, A. N.,31 Dec 2018,In:International Journal of Human-Computer Studies.120,p.1-1313 p.
Press accept to update now: individual differences in susceptibility to malevolent interruptions Williams, E. J.,Morgan, P. L.&Joinson, A. N.,30 Apr 2017,In:Decision Support Systems.96,p.119-12911 p.
Images by Laurie Lapworth/ University of Bath unless credited.
Video by Simon Wharf/ University of Bath

